Unggulan
- Dapatkan link
- X
- Aplikasi Lainnya
800 30 Risk Assessment Spreadsheet - CYB_407_Week 2 Assignment.docx - Week 2 \u2013 PracticeLab ... : Aircraft certification system safety process.
800 30 Risk Assessment Spreadsheet - CYB_407_Week 2 Assignment.docx - Week 2 \u2013 PracticeLab ... : Aircraft certification system safety process.. Information technology (it) risk assessment is the process of identifying and assessing security risks in order to implement measures and manage it risk assessment aims to help information technology professionals and information security officers minimize vulnerabilities that can negatively. Possible efb system risk assessment. Risk management is the process of identifying risk, assessing risk, and taking steps to reduce risk to an acceptable level. Then assessing, responding and monitoring. Recommendations of the national institute of they must also assess and incorporate results of the risk assessment activity into the decision making process.
.risk assessments nist risk management guide for information technology systems guide for conducting risk assessments nist tips for your next risk assessment based on nist 800 30 nist sp 800 30 nist nist risk management framework overview guide for conducting risk. Risk management is the process of identifying risk, assessing risk, and taking steps to reduce risk to an acceptable level. Um, how do we continue to monitor what we've assessed today. Prepare for assessment by identifying scope 2. An effective risk management program.

A risk assessment identifies and catalogs all the potential risks to your organization's ability to do business.
Nist 800 30 risk assessment template risk management framework rmf sdisac. The risk assessment methodology covers following nine major steps. Risk analysis, or risk assessment, is the first step in the risk management process. Why is risk assessment important? .risk assessments nist risk management guide for information technology systems guide for conducting risk assessments nist tips for your next risk assessment based on nist 800 30 nist sp 800 30 nist nist risk management framework overview guide for conducting risk. Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an. Dash 30 is what focuses in on the assessment piece and is gonna provide us with a very specific methodology what are the processes of risk assessments? There are many techniques used to carry out information security risk assessments. Frequently asked questions fedramp gov. Each risk might be ranked with adjectives such as low, medium, or severe. Risk management is a practical step in handling risk scenarios in an organization, including in the field of information security. A risk assessment identifies and catalogs all the potential risks to your organization's ability to do business. Aircraft certification system safety process.
Organizations use risk assessment, the first step in the risk management methodology, to determine the extent of the potential threat, vulnerabilities, and the risk associated. Prepare for assessment by identifying scope 2. Risk assessment is one of the core features of any health, safety or environmental management system. Possible efb system risk assessment. Risk assessment process identifikasi risiko mengenali peristiwa yang mungkin dapat terjadi dan berakibat negatif.
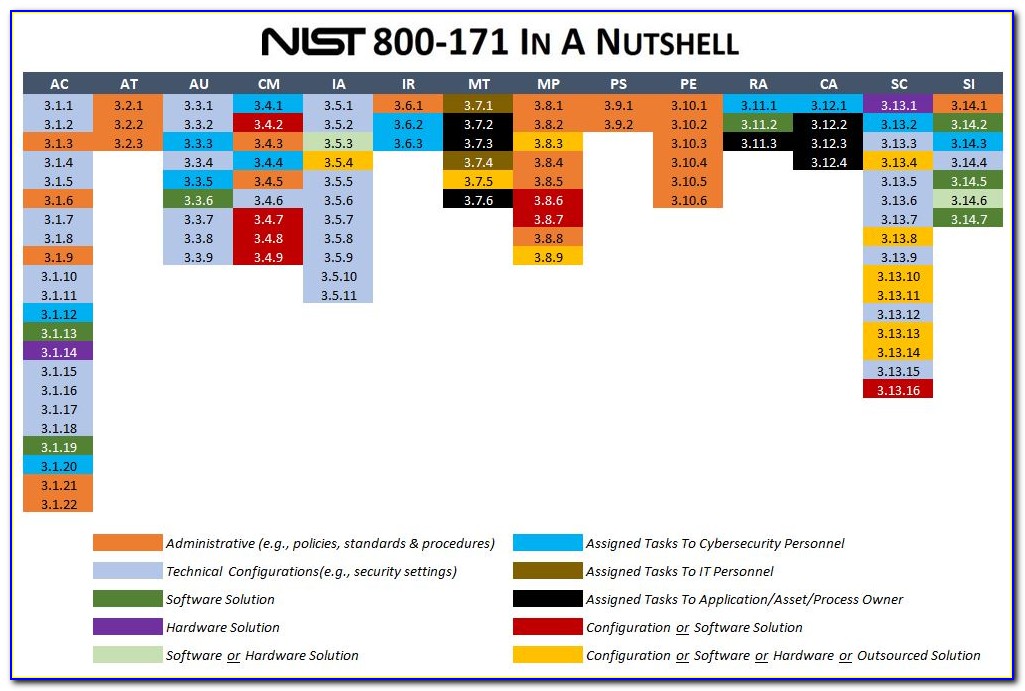
Aircraft certification system safety process.
A risk assessment identifies and catalogs all the potential risks to your organization's ability to do business. Um, how do we continue to monitor what we've assessed today. Frequently asked questions fedramp gov. What is efb security policy today ? The risk assessment process includes the following steps: Possible efb system risk assessment. There are many techniques used to carry out information security risk assessments. Risk management guide for information technology systems. Department/area name:_ this department reports to:_ person completing survey:_ briefly describe the department or area, its major. An effective risk management program. Risk management is a practical step in handling risk scenarios in an organization, including in the field of information security. Risk management is the process of identifying risk, assessing risk, and taking steps to reduce risk to an acceptable level. Then assessing, responding and monitoring.
Learn vocabulary, terms and more with flashcards, games and other study tools. Information technology (it) risk assessment is the process of identifying and assessing security risks in order to implement measures and manage it risk assessment aims to help information technology professionals and information security officers minimize vulnerabilities that can negatively. Possible efb system risk assessment. The assessment is broad in scope and evaluates security vulnerabilities affecting confidentiality, integrity, and availability. A risk assessment identifies and catalogs all the potential risks to your organization's ability to do business.
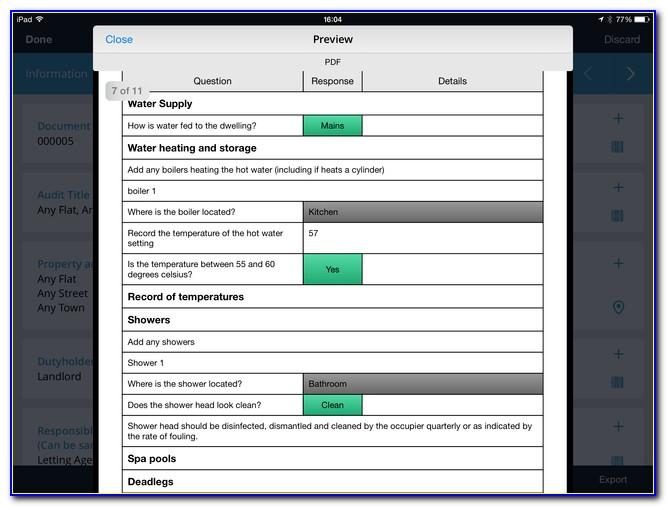
Learn vocabulary, terms and more with flashcards, games and other study tools.
Why is risk assessment important? Frequently asked questions fedramp gov. There are many techniques used to carry out information security risk assessments. .risk assessments nist risk management guide for information technology systems guide for conducting risk assessments nist tips for your next risk assessment based on nist 800 30 nist sp 800 30 nist nist risk management framework overview guide for conducting risk. Department/area name:_ this department reports to:_ person completing survey:_ briefly describe the department or area, its major. An effective risk management program. Risk assessment is one of the core features of any health, safety or environmental management system. Prepare for assessment by identifying scope 2. The assessment is broad in scope and evaluates security vulnerabilities affecting confidentiality, integrity, and availability. Um, how do we continue to monitor what we've assessed today. Risk management is the process of identifying risk, assessing risk, and taking steps to reduce risk to an acceptable level. Risk analysis, or risk assessment, is the first step in the risk management process. Guide for conducting risk assessments joint task force transformation initiative.
- Dapatkan link
- X
- Aplikasi Lainnya
Postingan Populer
Fiori Compleanno : mazzi di fiori per buon compleanno - Auguri Gratis - Sul nostro sito internet, puoi regalare fiori per il compleanno dei tuoi cari.
- Dapatkan link
- X
- Aplikasi Lainnya
Ceara De Zahar Pentru Epilat / Epilat cu ceara - Salon de frumusete - SUGAR Beauty Stuido / Traditionally one of the poorest in the country, certain regions have developed almost beyond recognition over the last 20 years, mostly from tourism and light.
- Dapatkan link
- X
- Aplikasi Lainnya
Komentar
Posting Komentar